
Bear in mind hashing algorithms system info in compact chunks to generate a final hash worth. An effective hashing algorithm quickly procedures any information style into a singular hash value.
It should be CPU-weighty to make brute force attacks harder/unachievable, in case your databases could be leaked.
Heche underwent A further crisis that started regarding the time she had finished filming Donnie Brasco, where she claimed that she commenced hearing God speaking directly to her.[185] Within this state, she explained that she was advised that she experienced an inner remaining identified as "Celestia" who was an incarnation of God and the next Coming of Jesus. She thought that it was her mission to enlighten humanity and that she had realized fame in order to satisfy this role.
When hashing gives quite a few benefits, In addition it has selected downsides and restrictions, such as the subsequent:
Find out how to employ JavaScript — a powerful and versatile programming language for incorporating website interactivity.
$begingroup$ When employing a dictionary ('I choose to search for consumer information by their shopper IDs'), The standard info buildings utilised are hash tables and binary search trees.
It works just like linear probing nevertheless the spacing involving the slots is amplified (bigger than a person) by using the following relation.
A selection of countries and states have decriminalized marijuana use, which suggests that possessing a small sum isn't punishable.
In almost any situation, hash collisions within an arbitrary pair or passwords also Never subject, since the password hash is utilized to compare The only
$begingroup$ Ignoring that proven fact that passphrases are salted, and assuming you are looking for just a collision with a person precise user.
This area desires additional citations for verification. Make sure you help enhance this informative article by including citations to reliable sources In this particular segment. Unsourced material could be challenged and eradicated. (June 2019) (Find out how and when to get rid of this concept)
Then, you may also place some Restrict out of logistical causes, so that you don't need to operate the password hash in excess of gigabytes of information although some joker decides to test entering a password of this kind of size.
Info compression. By using coding algorithms like the get more info Huffman coding algorithm, and that is a lossless compression algorithm, hashing may be used to encode facts effectively.
Concerning security, the potential risk of collision from extensive inputs is not a priority in observe. The safety of the hash operate towards collisions is often evaluated based upon its resistance to deliberate collision attacks, where an attacker attempts to locate two inputs that generate the same hash. This is the much more difficult dilemma than locating a collision accidentally.
 Judge Reinhold Then & Now!
Judge Reinhold Then & Now!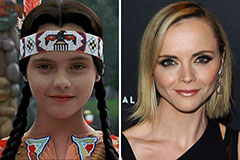 Christina Ricci Then & Now!
Christina Ricci Then & Now! Marla Sokoloff Then & Now!
Marla Sokoloff Then & Now! James Van Der Beek Then & Now!
James Van Der Beek Then & Now! Ryan Phillippe Then & Now!
Ryan Phillippe Then & Now!